CVE-2025-6264
Rapid7 Velociraptor Incorrect Default Permissions Vulnerability - [Actively Exploited]
Description
Velociraptor allows collection of VQL queries packaged into Artifacts from endpoints. These artifacts can be used to do anything and usually run with elevated permissions. To limit access to some dangerous artifact, Velociraptor allows for those to require high permissions like EXECVE to launch. The Admin.Client.UpdateClientConfig is an artifact used to update the client's configuration. This artifact did not enforce an additional required permission, allowing users with COLLECT_CLIENT permissions (normally given by the "Investigator" role) to collect it from endpoints and update the configuration. This can lead to arbitrary command execution and endpoint takeover. To successfully exploit this vulnerability the user must already have access to collect artifacts from the endpoint (i.e. have the COLLECT_CLIENT given typically by the "Investigator' role).
INFO
Published Date :
June 20, 2025, 3:15 a.m.
Last Modified :
Oct. 23, 2025, 1 a.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
Rapid7 Velociraptor contains an incorrect default permissions vulnerability that can lead to arbitrary command execution and endpoint takeover. To successfully exploit this vulnerability the user must already have access to collect artifacts from the endpoint.
Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable.
Known Detected Oct 14, 2025
https://docs.velociraptor.app/announcements/advisories/cve-2025-6264/ ; https://nvd.nist.gov/vuln/detail/CVE-2025-6264
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | MEDIUM | [email protected] |
Solution
- Enforce specific permissions for the Admin.Client.UpdateClientConfig artifact.
- Review and restrict COLLECT_CLIENT permissions for roles.
- Apply updates to Velociraptor as recommended by the vendor.
Public PoC/Exploit Available at Github
CVE-2025-6264 has a 1 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2025-6264.
| URL | Resource |
|---|---|
| https://docs.velociraptor.app/announcements/advisories/cve-2025-6264/ | Mitigation Vendor Advisory |
| https://blog.talosintelligence.com/velociraptor-leveraged-in-ransomware-attacks/ | Exploit Third Party Advisory |
| https://news.sophos.com/en-us/2025/08/26/velociraptor-incident-response-tool-abused-for-remote-access/ | Exploit Third Party Advisory |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2025-6264 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2025-6264
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
Detection artifacts for identifying Velociraptor misuse
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2025-6264 vulnerability anywhere in the article.
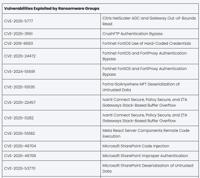
-
The Cyber Express
CISA Known Exploited Vulnerabilities Soared 20% in 2025
After stabilizing in 2024, the growth of known exploited vulnerabilities accelerated in 2025. That was one conclusion from Cyble’s analysis of CISA’s Known Exploited Vulnerability (KEV) catalog data f ... Read more
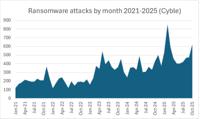
-
The Cyber Express
Ransomware Attacks Soared 30% in October
Ransomware attacks soared 30% in October to the second-highest total on record, Cyble reported today. The 623 ransomware attacks recorded in October were second only to February 2025’s record attacks, ... Read more

-
CybersecurityNews
CISA Warns Of Rapid7 Velociraptor Vulnerability Exploited in Ransomware Attacks
The Cybersecurity and Infrastructure Security Agency (CISA) issued an urgent alert on October 14, 2025, highlighting a critical vulnerability in Rapid7’s Velociraptor endpoint detection and response ( ... Read more

-
The Hacker News
Hackers Turn Velociraptor DFIR Tool Into Weapon in LockBit Ransomware Attacks
Oct 11, 2025Ravie LakshmananNetwork Security / Vulnerability Threat actors are abusing Velociraptor, an open-source digital forensics and incident response (DFIR) tool, in connection with ransomware ... Read more

-
The Register
Ransomware crims that exploited SharePoint 0-days add Velociraptor to their arsenal
The ransomware gang caught exploiting Microsoft SharePoint zero-days over the summer has added a new tool to its arsenal: Velociraptor, an open-source digital forensics and incident response app not p ... Read more

-
Daily CyberSecurity
DFIR Tool Hijacked: Ransomware Group Storm-2603 Abuses Velociraptor for Stealthy LockBit/Babuk Attacks
Cisco Talos has confirmed that ransomware operators are now abusing Velociraptor, an open-source digital forensics and incident response (DFIR) tool, in live ransomware campaigns. “Ransomware operator ... Read more

-
BleepingComputer
Hackers now use Velociraptor DFIR tool in ransomware attacks
Threat actors have started to use the Velociraptor digital forensics and incident response (DFIR) tool in attacks that deploy LockBit and Babuk ransomware. Cisco Talos researchers assess with medium c ... Read more

-
Help Net Security
Legit tools, illicit uses: Velociraptor, Nezha turned against victims
Threat actors are using an increasing variety of commercial and open-source products to carry out their attacks: according to researchers, Velociraptor and Nezha are the latest additions to their atta ... Read more

-
CybersecurityNews
Hackers Exploit DFIR Tool ‘Velociraptor’ in Ransomware Attacks
Security researchers at Cisco Talos have confirmed that ransomware operators are actively exploiting Velociraptor, an open-source digital forensics and incident response (DFIR) tool, in their attacks. ... Read more

-
security.nl
Cisco: open source DFIR-tool Velociraptor gebruikt bij ransomware-aanvallen
Aanvallers hebben bij ransomware-aanvallen gebruikgemaakt van Velociraptor, een open source tool voor digital forensics en incident response (DFIR), zo laat Cisco in een analyse weten. Volgens het net ... Read more
The following table lists the changes that have been made to the
CVE-2025-6264 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Oct. 23, 2025
Action Type Old Value New Value Removed Required Action Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable. Removed Date Added 2025-10-14 Removed Vulnerability Name Rapid7 Velociraptor Incorrect Default Permissions Vulnerability Removed Due Date 2025-11-04 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 22, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-6264 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-6264 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-6264 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-6264 -
Initial Analysis by [email protected]
Oct. 15, 2025
Action Type Old Value New Value Added CPE Configuration OR *cpe:2.3:a:rapid7:velociraptor:*:*:*:*:*:*:*:* versions up to (excluding) 0.74.3 Added Reference Type CISA-ADP: https://blog.talosintelligence.com/velociraptor-leveraged-in-ransomware-attacks/ Types: Exploit, Third Party Advisory Added Reference Type Rapid7, Inc.: https://docs.velociraptor.app/announcements/advisories/cve-2025-6264/ Types: Mitigation, Vendor Advisory Added Reference Type CISA-ADP: https://news.sophos.com/en-us/2025/08/26/velociraptor-incident-response-tool-abused-for-remote-access/ Types: Exploit, Third Party Advisory -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Oct. 15, 2025
Action Type Old Value New Value Added Date Added 2025-10-14 Added Due Date 2025-11-04 Added Required Action Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable. Added Vulnerability Name Rapid7 Velociraptor Incorrect Default Permissions Vulnerability -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 10, 2025
Action Type Old Value New Value Added Reference https://blog.talosintelligence.com/velociraptor-leveraged-in-ransomware-attacks/ Added Reference https://news.sophos.com/en-us/2025/08/26/velociraptor-incident-response-tool-abused-for-remote-access/ -
CVE Modified by [email protected]
Jun. 23, 2025
Action Type Old Value New Value Added CVSS V3.1 AV:N/AC:H/PR:H/UI:N/S:C/C:L/I:L/A:L Removed CVSS V3.1 AV:L/AC:H/PR:H/UI:R/S:C/C:L/I:L/A:L -
New CVE Received by [email protected]
Jun. 20, 2025
Action Type Old Value New Value Added Description Velociraptor allows collection of VQL queries packaged into Artifacts from endpoints. These artifacts can be used to do anything and usually run with elevated permissions. To limit access to some dangerous artifact, Velociraptor allows for those to require high permissions like EXECVE to launch. The Admin.Client.UpdateClientConfig is an artifact used to update the client's configuration. This artifact did not enforce an additional required permission, allowing users with COLLECT_CLIENT permissions (normally given by the "Investigator" role) to collect it from endpoints and update the configuration. This can lead to arbitrary command execution and endpoint takeover. To successfully exploit this vulnerability the user must already have access to collect artifacts from the endpoint (i.e. have the COLLECT_CLIENT given typically by the "Investigator' role). Added CVSS V3.1 AV:L/AC:H/PR:H/UI:R/S:C/C:L/I:L/A:L Added CWE CWE-276 Added Reference https://docs.velociraptor.app/announcements/advisories/cve-2025-6264/